Having problems with your PC? Nothing can't be solved, try to learn more about your computer software and hardware over here. Welcome to my blog!!
Here's what to do if you suspect an infection on your Windows PC. (Please note these steps apply to both Windows XP and Vista.)
1) Are you sure it's spyware or a virus? Windows pop-ups and alerts can often seem invasive enough to be viruses, especially with Vista. Try searching the web for the exact text you see on the screen to make sure you aren't dealing with an aggressive Windows message. (Many of these can be turned off, so try whatever instructions you find.) On the other hand, some viruses masquerade as Windows alerts, so tread lightly.
2) Boot in safe mode. If you have a virus, first step is to try booting in safe mode. You can get to safe mode (a simplified version of Windows that disables a lot of extra gunk, possibly including some spyware apps) by restarting your PC and tapping F8 during boot. Soon you'll get a menu of options. Select "Safe Mode" (it's at the top of the menu) and wait for the machine to fully boot. The system will look funny (with a black background and larger icons, probably), but don't worry about it. This is only temporary. (Also note that many spyware applications can disable safe mode, so if you find this doesn't work, just boot normally.)
3) Run your antivirus application. This is of course assuming you have an antivirus application. (Need one? Check here.) You're in safe mode now, so run a full scan of your PC at maximum security levels (include the option to scan within compressed files, for example). This will probably take an hour or more, so be patient. Fix any problems the virus scan turns up. Then reboot into safe mode again using the procedure in step 2.
4) Run one or two anti-spyware applications. I used to recommend running multiple anti-spyware apps, but virtually all antivirus apps now do a pretty good job at getting rid of spyware too, so you don't need an army of additional applications just for spyware. Also, I now recommend starting with AdAware (which is free) and moving on to Spyware Doctor (free as part of the Google Pack) if you feel you need additional help. (Please note that recent versions of Spyware Doctor and Norton Antivirus have some trouble with each other.) You can try other apps too, but the once-recommended SpyBot Search & Destroy is no longer very effective, sadly. (Neither is Microsoft's own Windows Defender.) Of course, fix anything and everything these apps find.
5) Reboot normally. (Not in safe mode.) Now take stock. Still got spyware? It's time to move along to my more advanced techniques for removing the nasties.
6) Run HijackThis. HijackThis is a free software tool that scans your computer to find malware that other apps might miss. Scroll down to "Official downloads" to download the tool. Next, simply open the ZIP file you downloaded, extract the application, and run the tool (you don't need to install it). Click the "Do a system scan and save a logfile" button. You'll receive a large text file as well as a dialog box which gives you a list of active software processes, which you can then choose to delete. Unfortunately, this list includes both helpful and unhelpful software, so don't just start deleting items. Continue in step 7 to figure out how to fix your spyware infection.
7) Post your log file online. Visit this page, which offers a list of forums staffed by volunteers who can help you interpret your HijackThis log. The SWI Forums are especially busy, but most of the forums on the list are equally apt. Go to SWI and visit the "Malware Removal" forum which has over 50,000 topics listed: Those are all people like you who are seeking help getting rid of spyware. Register for an account, read the FAQ, then visit that Malware Removal forum, and post a new topic. Paste the content of the text file you created in step 5 into this topic and (politely) ask for help. You will get a response from a volunteer helper, typically within 3 days. You'll be given specific advice on what entries to remove with the HijackThis tool, and you might be pointed to additional software to run to help remove common spyware infections. Follow all the instructions and keep working with the forum helpers until either you or they give up. (And no, don't send your log file to me or post it here. I am not nearly the spyware removal expert that these guys are.)
7a) Alternately: Paste your log file into an automated tool. Don't have three days? Try simply pasting your HijackThis log file into this form. It does a pretty good job at auto-analyzing what's wrong with your machine, with no waiting. As well, if that doesn't work, you can search for the items you find in the HijackThis log by name to see what they are and how to remove them, if they're spyware. This can be quite time consuming, though.
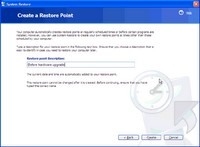
8) Try System Restore. If that doesn't work, you might try running Windows System Restore to roll back your OS to a time before the infection happened. This isn't foolproof: You might not have System Restore turned on, or the spyware might have shut System Restore off, as well. But it's worth a shot. With either XP or Vista, System Restore can be found under Start > All Programs > Accessories > System Tools > System Restore.
9) Give up and wipe your hard drive. At this point, you've exhausted all the options I know of. You might try again at steps 6/7 to make sure you've done everything you can to salvage the PC. Forum helpers will often work with you for weeks to help fight a spyware infection, but there are tens of thousands of possible variants out there, with new ones cropping up every day. It's just not possible to clean them all, every time. Sometimes the only thing you can do is call it quits, reformat your hard drive, and reinstall your OS. Again, make sure you have your backups ready and verified. Once you're up and running, reinstall your antivirus and anti-spyware applications, and stay vigilant against infection. Good luck.

Comments:
I have been using IE for years and the performance is under my expectation. Furthermore, many problems like Pop-up advertisements, Spyware..... have been started to attack my PC. One of the main factor of crashing my PC recently was due to IE.
When IE problem occurred, I have decided to use other Website Browser like Netscape and Mozilla FireFox. I learned that, other browser didn't cause me the same problems like Pop-up...so and so. So what is Microsoft doing? What should we do? Continue using IE or Stop?
I think there are many reasons of people attacking IE, one of the main reason is its popularity. When you have planned to attack someone make sure the "bom" hit the important areas right? Other reasons, maybe IE is part of Windows, where Windows will not working or instable if IE dead.
So, My recommendation to you is not to use IE for browsing the internet. The award-winning, free Web browser is better than ever. Browse the Web with confidence - Firefox protects you from viruses, spyware and pop-ups. Enjoy improvements to performance, ease of use and privacy. It's easy to import your favorites and settings and get started. Please try to install Third part Netbrowser as follows:
Mozilla FireFox: http://www.mozilla.com/firefox/
Netscape: http://browser.netscape.com/ns8/

Also, There are many Free Trial AntiSpyware offered on internet. I have tried some in the past and they are all LIAR. After I have installed those softwares on my PC, it become worst than before. I strongly believed that these so-called ANTISpyware or AntiVirus company are actually Spyware or Virus creator. I think this kind of business is worst than a ROBBER.
Finally, I chose to reformat my Hardisk and end the problems.
1. Open Backup. (Click Start, point to All Programs, point to Accessories, point to System Tools, and then click Backup.)Choosing what to back up
2. The Backup or Restore Wizard starts by default, unless you disabled it. If the Backup or Restore Wizard does not start by default, you can still use it to back up files by clicking the Tools menu, and then clicking Backup Wizard.
3. Click the Next.
4. In the Window that asks What do you want to do? click the circle next to Back up files and settings. Then click Next.
To learn more about the Windows XP Backup Utility read Backup Made Easy.
Case 2: Copy and Paste to external backup device or CD or DVD
But the follwoing way is recommended:
Install version 4.1.4E of Palm Desktop with cautionVersion 4.1.4E was designed for devices with extended fields. For example, you can store up to three addresses for a person with the extended PIM fields; on previous devices, you could store only one address. If you install this version of Palm Desktop on an older device, you will only be able to sync with the fields on your Palm device. In this example, although you can store three addresses for a person in Palm Desktop, only the first address will be synchronized with your older device. The extended PIM fields will not sync with the older device.
Examples of extended fields not available on older devices (these may appear in Palm Desktop 4.1.4E but will not sync with older devices):
1) Contacts (Address Book): Picture, Birthday, IM address, Website, more than one address.
2) Calendar (Date Book): Location, Category
3) Tasks (To Do List): Repeating tasks, completion date, timed alarms
4) Memos (Memo Pad): More than 4,000 characters in a memo item
If you install the 4.1.4E version and then uninstall and go back to version 4.1.4, your Palm Desktop user files will no longer be compatible with the older version. These files will need to be regenerated from your device's data.
If you're comfortable with this option, download version 4.1.4E from this site.
The next page will be the End User License Agreement. When you click "I Agree," a file named PalmDesktopWin414E.zip will begin to download.
Download time: Please note, this file is 42MB. On dial-up connections with a 28.8 modem, expect to spend about 30 minutes downloading the software.
Palm Desktop for Windows FAQ
Start > All Programs > Compaq > Compaq PC Tools > Compaq
System Recovery or
Start > All Programs > Compaq > Compaq Presario
PC Tools > Compaq System Recovery or
Start > All Programs > PC Help & Tools > Compaq System Recovery.